Netflix signs traffic deal with Verizon

Now that Net Neutrality is dead in the United States, the agreements for preferential traffic will start to be signed. Netflix had signed a deal with Comcast last February to have a direct link with the ISP, with Reed Hastings, Netflix CEO saying at the time that preferential treatment violates their…
NASA Tech Transfer Software Catalog
NASA released their catalog of software that they are willing to share with some people, and they did it in a very original way – a 127 pages long .pdf file, with the name, reference and a small description of each of those programs and libraries. Unfortunately most of the…
Tactus – Buttons when you need them
Coordinated microbots
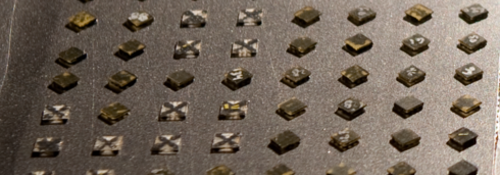
SRI International’s senior researcher Annioe Wong-Foy demonstrated a group of small robots working together to make structures bigger than them. Each individual robot is very simple and have only one or two metallic arms that allow it to make a set of predefined operations, but using several of this microrobots it’s…
OnePlus – the CyanogenMod phone
Vulnerabillity in World Airline Network
Samsung Galaxy S5 fingerprint spoofed

Another phone with fingerprint authentication, the same spoofed fingerprint to bypass it. After the Chaos Computer Club released their finding on how to bypass the fingerprint authentication of the iPhone 5S only 2 days after it was released, it was now the turn for Galaxy S5 to suffer similar faith only 4…
Pyro Board – 2D Fire visualization board
Putin tells Snowden he doesn’t spy on Russians
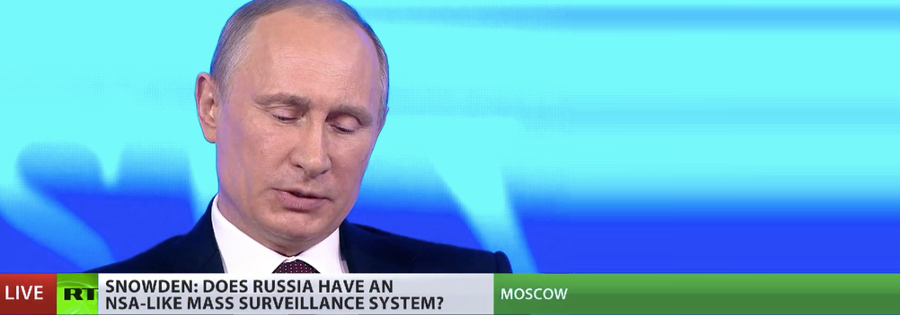
Edward Snowden, the guy who told the world about the NSA mass surveillance pratices is now living in Russia, and decided to ask Vladimir Putin, the Russian president, about the existence of similar pratices in Russia. Putin told that Russia doesn’t have similar practices, that the country doesn’t even the…
Obama leaves loophole open to exploit zero-day vulnerabilities

Barack Obama is said to have left a big loophole in a directive telling the american national security and law enforcement communities to disclosure vulnerabilities they find in software. This directive is supposed to open an exception for “a clear national security or law enforcement need.” – that the NSA sees…